Authentication
The third-party API is designed to allow access to endpoints owned by tenants other than the operator's (third-party developer) tenant. An operator will make use of an Identity client ID/secret pair in conjunction with their tenant ID to request bearer tokens. Each request through the third-party API will be aimed at a target tenant and provided with the operator's bearer token. The authorization mechanism will ensure that the operator's tenant is authorized to make changes to the target tenant's endpoints.
All operations require authentication or return additional information if you are authenticated. As a third-party developer, you are authenticating and getting authorization to act on a utility tenant's behalf. Additionally, you can make more requests within five minutes when you are authenticated. Bearer tokens expire after 60 minutes so any requests made before token expiration don't require a new bearer token.
Authenticating
This section describes the mechanism by which you obtain an OAuth token used to authenticate and authorize your use of the APIs.
Authorizations throughout the API communications are authenticated using JSON Web Token (JWT). JWT is an open standard that defines a compact and URL-safe method for securely transmitting information as a JSON object between parties. A JWT is often used to secure RESTful APIs because it can be used to authenticate a client that wants to access the APIs.
JWT security scheme type is HTTP, HTTP Authorization scheme is bearer, and the bearer format is "JWT".
For more information and for an example authentication request, see Obtain a bearer token from Itron Identity.
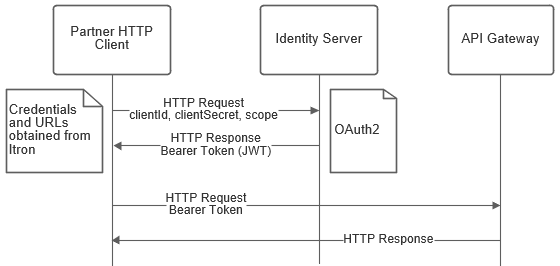
The following sequence diagram illustrates the authentication process of obtaining a token.