Granting AAD access for service principals
In order to grant the permissions requested by the registered application to the service principal, consent is required. End users or an administrator may provide consent, depending on the level of access prescribed by the registered application:
-
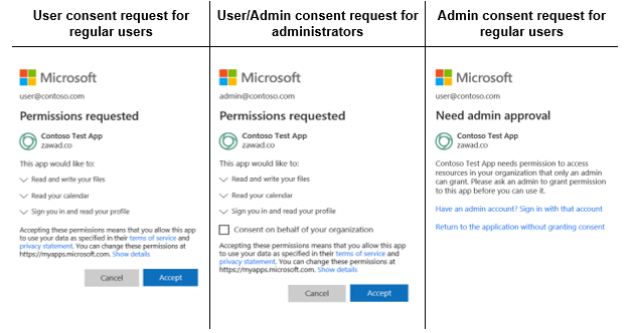
User consent. Occurs automatically during the OAuth 2.0 authorization flow. If the user (or administrator, as appropriate) has not yet granted consent for this app, then Azure AD will prompt the user to provide consent at this time.
-
Admin consent. Required when the app needs access to certain high-privilege permissions. Admin consent ensures that administrators have some additional controls before authorizing apps or users to access highly privileged data.
Note: An administrator can also consent to an application's delegated permissions on behalf of all users in the tenant. This prevents the consent dialog from appearing for every user and can be done from the Azure portal by users with the administrator role.
Consent request prompts may vary according to user type and consent type, as shown in the following examples.
Creating a service principal is allowed for end users by default in any newly created AAD, but this privilege can be revoked via the Azure Portal.
On the Azure Portal User settings screen, the App registrations section provides Yes and No buttons to indicate whether users can register applications. To enable users to register applications, select Yes.
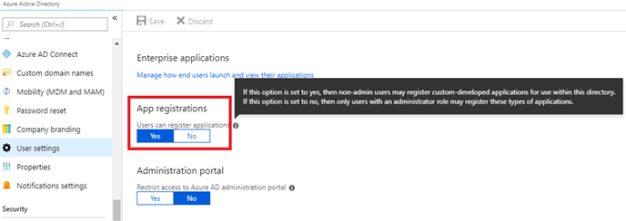
With this setting in place, all users (except for administrators) will be prompted by a Need admin approval form until an administrator grants the requested permissions for any new application.